Ransomware: Using Qualys in the enterprise
Ransomware has risen by over 250 percent during the first few months of 2017, according to a report Monday by the security firm Kaspersky. The publication of the cybersecurity statistics, which revealed that the U.S. is the country worst affected by the issue, comes as experts warn of a ransomware epidemic in the wake of the WannaCry cyberattack.
The Kaspersky Lab Malware Report for the first quarter of this year revealed that the number of ransomware files detected had reached 218,625, compared with 61,832 in the previous quarter. Devices compromised by ransomware mean the owner must pay a ransom in order to recover their data.
So the question is... how do I determine if my organization is at risk? How do I efficiently and quickly check to see if any device could be a springboard or used for ransomware?
Many organizations will often run scans to seek out the vulnerability that permits ransomware to infect the device and often others. But those scans can take quite a bit of time and we need to know now!
Qualys has very efficient ways that are expedient and very accurate.
KNOW THE EXPLOIT
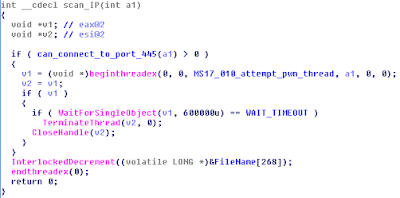
The first step is knowing the exploits method of delivery. Often it is a flaw within an OS. In the case of WannaCry, it exploited the SMB flaw in MS17-010.
NARROW THE SEARCH
In this case (WannaCry), we see that it uses port 445 (the name resolution port for Windows). Given we know the port and the MS security bulletin #, we can now begin to create a very succinct search.
We can now use the KB in Qualys to look for the QID. By going to the KB tab in the Vulnerability Management module, perform a search and look for MS17-010.

CREATE THE SCAN
There are steps to this and one optional.
Note: It is assumed you are familiar with Qualys and understand how to create the general elements to run a basic scan.
First, create a search list. Give it a name and apply the QID to the list.

Second, create the option profile. Select "none" under TCP ports and "445" under additional. Under UDP, select "none".

Third, under Scans in the option profile, there is a section called "Vulnerability Detection". Choose custom and select the Search List you created in step 1.

A fourth and optional step is to enable parallel scaling. Some VM's have more robust resources and can handle more tasks. By default, this is turned off but if you want to enable the scanners to increase the workload by utilizing their power, make the following changes:

START THE SCAN
Finally, create a scan job. Be sure to select the proper option profile, select as many scanners to run as you can, select the Ultimate priority setting and kick off the job.
It will run very fast and ONLY search for that one QID on a single TCP port in the enterprise.

Comments
Post a Comment